How To Know If Your Phone Has Been Hacked will be described in this article. Is something off with your phone? Someone could be hacking. Regretfully, there is always a risk of phone hacking, which might compromise your device’s functionality and reveal your personal information. Learn the warning symptoms of phone hacking and what to do if you become a victim by reading on. Next, safeguard yourself by downloading Avast One, a free mobile security program.
How To Know If Your Phone Has Been Hacked
In this article, you can know about How To Know If Your Phone Has Been Hacked here are the details below;
What is phone hacking?
The act of gaining unauthorized access to a smartphone’s data, communications, or communications is known as phone hacking. Phone hacking can take many different forms, such as listening in on phone calls or collecting personal information. A phone can be hacked in a number of ways, such as through tracking software, phishing attempts, and unprotected Wi-Fi networks.
This Article Contains:
- What does phone hacking entail?
- Indices that someone has hacked your phone
- How is my phone hackable?
- Which smartphones are simpler to hack, Android or iPhones?
- How to respond if someone has hacked your phone
- How to prevent pirates from accessing your phone
- Defend against intrusions using robust security software.
- FAQs
Due to their large amount of stored personal data, phones are often targeted by hackers. Email addresses, phone numbers, bank account information, and website login credentials are all stored on smartphones. This data can be used by hackers for a variety of cybercrimes, including identity theft and the sale of the information on the dark web.
Signs your phone has been hacked
Cybercriminals are always improving their techniques, which makes it harder to identify their attacks. Remember that hackers have the ability to remotely deactivate your phone, so you always need to be one step ahead. Thankfully, you may tell if you’ve been targeted for phone hacking by looking for some telltale indications.
The following are typical indicators of phone hacking:
Pop-ups
You may have an adware infection on your phone if you’re seeing a lot of pop-up advertisements. Even with ad-blocking turned on, if the issue continues, it may indicate possible hacking. Avoid clicking on or opening these pop-ups at all costs, as doing so may exacerbate the issue.
Unrecognized texts or calls
If you start receiving messages from unknown numbers, it may be a sign that your data has been compromised. Unless you can confirm their legitimacy or are expecting the call, never take calls from numbers you are not familiar with.
Any contact on an iPhone or Android phone that has been hacked can receive text messages. Your number might be next if someone you know has had their phone compromised. Look through your call logs for any strange activity, and if you come across a number you don’t know, you might want to report it as spam and block the contact.
High data usage
Your phone hacker may be to blame if your online activity hasn’t changed much but your data usage has increased dramatically. Unusually high data usage may be the result of a malicious program operating in the background. Examine your apps and remove anything that seems off.
High battery drain
Do you frequently charge your phone? Does your battery run out of power far faster than it used to? It’s possible that your phone is merely becoming older or that there’s a problem other than a dead battery. Unwanted apps that have been placed on your phone through hacking or other illegal methods have the ability to quickly deplete your phone’s battery life.
Hot phone
Even when you’re not using it, is your Android or iPhone getting hot and remaining hot? Like any devices, your phone may get heated from extended use, particularly if you’re streaming or playing games for extended periods of time.
However, if that’s not the case and your phone is still feeling too warm, it could be overheating due to malicious software.
Reduce performance
Are calls from your phone dropping? Do you not receive SMS, or do your texts not reach their intended recipient? Is your phone constantly stalling, crashing, or restarting itself without warning? Malware or undesired background apps could be the source of your phone’s processing power waste.
After eliminating hackers, think about repairing Android apps that crash.
Websites look strange
You may be redirected to undesirable, malicious websites by a malware-infected iPhone or Android phone that has been hacked. Websites that appear strange to you may have recently undergone a redesign, or it could indicate that you accidentally navigated to a dangerous website.
Unexpected charges on your phone bill
Unwanted apps may be using up more of your data than usual, which could result in surprise charges if your phone bill is greater than usual. Apps that install malware inflate your bill with unnecessary expenses, and if someone has remote access to your phone, they may misuse your subscriptions and other services.
Consider canceling any unnecessary subscription costs that are showing up on your phone bill, and remove any malicious apps right once.
Changes to settings
If you see sudden, strange changes to your phone’s settings, it’s a dead giveaway that it has been hacked. For example, if you discover that the permissions for your camera or microphone have changed, it can be because hackers are attempting to watch what you do. It is very suggestive that your phone has been compromised if you discover that your privacy and security settings have been altered.
Apps you don’t recognize
Unusual applications that you haven’t downloaded ought not to be on your phone. A phone hacker may be to blame if you discover an app on your phone that you did not install. Naturally, new phones have some pointless apps pre-installed (called bloatware). It doesn’t always follow that a program is harmful just because you can’t recognize it.
Everybody has a varied phone usage pattern. Older phones or phones with little storage space might occasionally exhibit symptoms similar to those of a compromised device. Therefore, you shouldn’t presume that you’ve been hacked right away.
Latest hacking news-November 2023
- TikTok frauds are on the rise because to AI | Avast
- You might find ChatGPT | Avast to be your next online match.
- Android malware is being installed by hackers via WhatsApp messaging | GBHackers
- Using new spyware, cybercriminals steal banking information | ABC News
- Google strives to prevent Android phones from running malicious apps | Phone Arena
However, you should act right away if you discover odd apps that are difficult to uninstall, see unexpected charges on your bill, or encounter other issues that point to a malware infection. See our instructions for eliminating malware from iPhones and viruses from Android devices.
It can be difficult to detect when you’ve been hacked at times. Avast One, or any other mobile antivirus program, will automatically protect your phone from hackers. Before you install any dangerous apps, Avast One performs routine security checks on your smartphone to identify potential dangers. Additionally, it guards against other internet dangers including sites that include malware.
Common signs of phone hacking
How can someone hack my phone?
The majority of phone hacking incidents occur following an action taken by the target or victim, such as clicking on a malicious link. A phone hacker will frequently use a mix of technological deceit, social engineering, and exploiting security flaws to deceive victims.
The following are a few of the most typical methods for phone hacking:
Phishing
Phishing is a type of targeted cyberattack wherein victims are tricked into downloading a harmful attachment, clicking on a malicious link, or sending sensitive information. Getting private information from a victim is the goal.
Phishing attacks are generally sent via text message or email. In a tactic called spear phishing, the attacker may bait certain persons or groups or throw a wide net. For a hack to occur, all that is required is a convincing email or iPhone message. Hackers can access a variety of accounts and devices, including your phone, based on the confidential information they manage to obtain.
Tracking software
Device activity is tracked and recorded by tracking software. Web monitoring can be legitimate, but occasionally hackers or even family members use it as malware to capture and steal personal information. A powerful contemporary example is the use of Pegasus spyware against journalists, activists, and politicians.
Hackers can also record your phone’s keystrokes and save sensitive data like credit card numbers, passwords, login credentials, search searches, and other information by using keyloggers and other monitoring software.
Wi-Fi and Bluetooth
Hackers can quickly infiltrate unprotected wireless networks, steal confidential data, and listen in on private conversations. For secure and private browsing on public Wi-Fi, use a VPN to guarantee an encrypted connection.
Avoid pairing your phone with an unidentified Bluetooth connection since hackers are capable of breaking into Bluetooth devices as well. Study up on the most secure Wi-Fi connection types and discover how to detect if your Bluetooth has been compromised.
SIM swap attack
A SIM switch attack occurs when thieves use personal information that they have obtained through phishing or that you have disclosed publicly on social media to fraudulently request a new SIM card from your mobile service provider. A hacker with complete access to your phone number could receive all of your texts and calls thanks to a SIM switch assault.
A SIM swap attack’s primary objective is usually to use 2FA texts to obtain unauthorized access to your bank account or other accounts. By establishing a challenging security question with your service provider, you may prevent SIM swap attacks in addition to adhering to privacy and security best practices to secure your personal data.
USB cable
Rarely, but some phony USB cables are set up to wirelessly transfer data to a hacker’s PC. Fakes and authentic Apple iPhone cables might be nearly identical. Make sure you only purchase authentic phone accessories from authorized retailers, and stay away from connecting cables or other hardware that belongs to someone you don’t trust.
Trojans
Although Trojan horse software appears to be a genuine program, it is actually loaded with harmful code meant to damage your device or steal data. Although trojans are much more prevalent on Android devices, Apple evaluates apps on their App Store rather carefully. For this reason, you should install one of the top antivirus programs to detect any malware that may get past Apple’s stringent security measures.
Cryptominers
Cryptominers create cryptocurrency by utilizing the processing power of your smartphone. Cryptojacking is the term for hacking that is carried out without your consent and is similar to cryptomining. However, even “legit” cryptomining apps have the potential to use your phone so aggressively that legal overheats and malfunctions. It may also jeopardize the security of your device in other ways.
What’s easier to hack: Android phones or iPhones
Due to the fact that more individuals and more phones run the Android operating system, there is a bigger pool of likely targets for phone hacking on Android phones than iPhones. However, iPhone users are still at risk because phone hackers are increasingly focusing on iPhones.
In other words, iPhones are susceptible to hacking, much like Macbooks. However, because the Android operating system is more open, Android devices are typically easier to hack.
The operating system for the iPhone, iOS, is a closed development environment. Apple does not provide system or app developers with access to its source code, and its devices cannot be altered (unless you jailbreak them). Hacked iOS devices are more difficult to manipulate since it is more difficult for software engineers to get programs approved on the App Store and deployed onto iPhones.
On the other hand, Google developed the open-source Android operating system. Android allows developers of apps and systems to access its source code. This facilitates the creation of plugins, upgrades, and other changes by developers. Additionally, although this promotes creativity, it also makes Android devices more vulnerable to hacking.
Always keep your phone updated to address operating system flaws and patch exploitable security vulnerabilities, regardless of the phone you use. Additionally, only download software from reputable stores like Apple’s App Store or Google Play.
What to do if your phone has been hacked
Take immediate action to minimize the harm if your phone has been compromised. You can take easy measures to reduce the risk and restore your phone from hacking. Also check Remote Coworker Alternatives
What to do if your phone is compromised is as follows:
Delete unrecognized apps
Remove the harmful software first. Examine each app you have and make sure nothing strange is there. Malware that impersonates a background software and is harmless can be installed by hackers. Check the authenticity of any apps you are unsure about, and remove those that seem dubious.
Run anti-malware software
Your phone will be scanned by a powerful malware scanner and removal tool to find and eliminate any harmful content. This is a crucial step because if you overlook assault residues, the problem can resurface.
Restore the device
The majority of malware can be eliminated via a factory reset, but all of your phone’s data will be lost. Prepare a backup of all of your contacts, pictures, notes, and other data before you reset your phone.
Resetting your phone is the ultimate last option when it comes to dealing with a hijacked smartphone. Take caution as you can lose vital files.
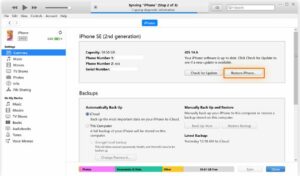
How to restore your iPhone to its factory settings
Resetting your iPhone will obliterate all of its settings and data, but it will also clear it out if you need to reset an iPhone that has been hijacked. Make a complete backup of your iPhone before restoring it to avoid losing any crucial data.
To factory reset your iPhone, observe these steps:
- Launch iTunes, select the iPhone icon, and secure your phone to your computer over a USB connection.
- Click Restore iPhone, then adhere to the prompts displayed on the screen.
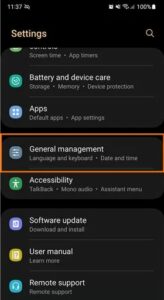
How to restore your Android phone to its factory settings
You can return your Android device to its factory settings if you need to start over. As everything will be deleted, be sure you have a backup of your important files.
Here’s how to return your Android phone to its original configuration:
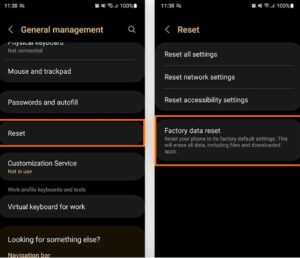
- Choose General management from the Settings menu.
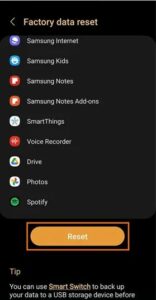
- To reset factory data, tap Reset.
- Press and hold the Reset button to confirm.
Reset your passwords
Change your previous passwords and the access code on your phone if you’ve been hacked. Additionally, update the passwords on every account that is linked to your phone. This includes the login information for all of your phone-connected accounts, including social media, cloud-sharing, and online banking. Create secure passwords at all times to avoid future security lapses.
Delete strange apps from your phone right away, scan for malware, recover your device, and change your passwords if your phone has been compromised. In the event that your phone has been compromised, do all of the above.
Inform your contacts
It’s crucial to notify your contacts if your phone has been compromised since it’s conceivable that the compromised device was used to send spam, phishing, or other scam or fraudulent communications to people you know. Advise them not to interact with any weird messages or click on links, as they could end up being the next victim.
Inform your service provider
Contact your mobile service provider so they may freeze any unauthorized movement, restore your phone digit, & resecure your account by counting a PIN or security question. A hacked phone may be sending messages and calls to a hacker’s device.
How to protect your phone from being hacked
It’s not enjoyable to fix your phone and protect your personal information after a compromise. It’s crucial to make sure it never occurs in the first place because of this. You can secure your devices and personal data while fortifying your defenses against phone hacking with routine maintenance and excellent digital hygiene.
The following are the best security procedures to avoid phone hacking:
- Make use of strong passwords; weak passwords are simple to figure out. Make complex, one-of-a-kind, difficult-to-guess passwords or passphrases to keep hackers at bay. Use one of the greatest password managers to manage all of your accounts and avoid using the same passwords across them. One of the greatest methods to keep hackers out of your phone is to use strong passwords.
- Employ biometrics and two-factor authentication (2FA): With 2FA, hackers require more information to access your accounts than just your password. Additionally, facial recognition and other biometric technologies can help deter hackers, even though the use of biometrics by the government is questionable. Make sure you conduct preliminary research.
- Delete your browsing history and cookies: A profile of your online activities can be built using the digital footprint you leave behind. To protect your privacy, remove the cookies from your browser.
- Update your software: It is always changing. Developers can address bugs and patch security holes with updates. Make sure your programs are up to date by establishing software updates on a regular basis.
- Use antivirus software: Malware and hacks can get through even the most careful defenses. Strong antivirus software should be used on a regular basis to provide you with real-time security by identifying and eliminating threats on your phone as they arise.
- Download and install Avast Mobile Security for Android on your Android phone. Additionally, install Mobile Security for iOS on your iPhone.
- When using public Wi-Fi, use a VPN: Insecure networks are easily penetrated by hackers. To secure your connection and shield you from prying eyes, you require a VPN.
- Avoid jailbreaking: Jailbreaking, also known as rooting, is the process of changing the fundamental software to get beyond limitations imposed by manufacturers or developers. Jailbreaking involves making changes to the operating system of your phone. It increases your vulnerability even though it gives you the ability to perform root adjustments to your phone. Without the original operating system’s built-in security, hackers are more likely to hijack your phone and install malware.
Protect your phone against hacking
Lock your SIM card
Since many SIM cards come with “1234” as the default password, locking your SIM card and changing your PIN is one method to stop someone else from accessing your texts or phone calls. But be careful—it might not be possible to get back in if you lock yourself out of your own SIM due to forgetting the PIN.
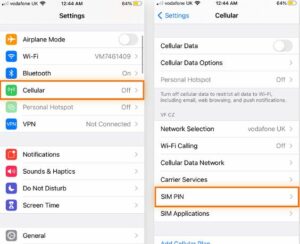
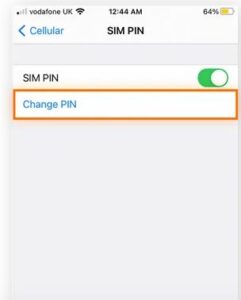
Here’s how to modify an iPhone’s SIM PIN:
- Select Settings, Cellular, and then SIM PIN.
- After confirming that the SIM PIN is toggled on (green), select Change PIN, enter your new PIN, and make sure you remember it.
Turn off your Wi-Fi and Bluetooth when not in use
By closing the “air gaps” between your device and the internet and Bluetooth, hackers are unable to remotely install malware or retrieve data from your phone. In addition to guarding against hacking in the first place, disabling Bluetooth and Wi-Fi enables you to do an antivirus check and ensure that no malicious software is left on your phone. Also check LeetCode Alternatives
Avoid storing sensitive information on your phone
You are less susceptible to hacking attempts the less identifying information you have on your phone. Eliminate any images, notes, files, or applications that might contain sensitive information, like:
- ID card and passport scans
- Date of birth or location of birth
- Complete names of your siblings or parents
- Your parents’ or siblings’ birthdays
- Your maiden name or complete name
- Specifics of your most recent travels
- images of your credit cards
Protect against hacks with strong security siftware
Our personal lives are inextricably linked to our phones, from images to money. Maintaining proper digital hygiene is crucial to preventing hacking. Avoid taking the chance of having your phone hacked and having your personal information stolen.
In the event of a malware attack, Avast One will identify the threat and notify you. In addition, it will guard your browsing with a web shield, automatically check your phone for threats, and shield you from other online scams. With Avast, transform your phone into a stronghold.
FAQs
Can a phone be hacked when turned off?
Most hacking attempts are thwarted by turning off a phone because code typically cannot run without an internet connection. The more recent iPhone models, on the other hand, go into a low-power state rather than shutting down entirely, enabling the use of apps like Find My iPhone. It’s possible that in the future, hackers will take use of this functionality.
Can you get hacked by answering a phone call?
Simply answering a call placed through your network service provider cannot lead to a hack. However, this does not preclude the possibility of a phone call being used as a means of social engineering attack to breach your security.
Can you get hacked through WhatsApp?
If you click on a nasty link or attachment, WhatsApp can be used to steal your account. Additionally, accepting a WhatsApp call has the potential to install malware on your phone, so you should be cautious when answering calls or messages from unknown numbers. Moreover, to take advantage of the most recent security updates, keep WhatsApp updated.
Can your phone camera be hacked?
It’s feasible for someone to break into your phone and spy on you in real time if your device has been compromised. You may accomplish this remotely via a Wi-Fi network, which is just one of the several benefits of using a VPN whenever you utilize unprotected public Wi-Fi.
Can a website hack your phone?
Through clever drive-by downloads, phony or malicious websites can infiltrate your phone and start an assault without requiring any user input from you, such as connecting a connection or downloading a file. Malvertising pop-ups and banners can be used by hackers to infect your device, even on reputable websites.